Automated brand impersonation protection has become a baseline requirement for digital security. As phishing operations scale across web domains, mobile app stores, social platforms, and ad networks, attackers are moving faster and operating more broadly than ever before. Traditional defenses – periodic scans, manual takedowns, post-incident analysis – are too slow and too shallow. Today’s security teams need a real-time system that detects brand impersonation threats from the earliest reconnaissance stage through live user engagement, and neutralizes them before customer trust, credentials, or revenue are compromised. Globally, the financial impact of phishing attacks reached an estimated $3.5 billion in 2024, including direct losses and remediation costs, underscoring the need for a shift in, not just tactics, but overarching strategy.
What Is Automated Brand Impersonation Protection?
Automated brand impersonation protection refers to a system that detects and disrupts impersonation threats across digital environments, in real time and without manual intervention.
Unlike traditional tools that rely on post-facto scans or user reports, automated systems:
- Monitor across domains, mobile apps, social media, and ad networks
- Detect early-stage signals such as domain registration and reconnaissance activity
- Detect real-time user exposure signals at the browser or device level
- Disrupt scams during live sessions using credential decoys and alerting systems
- Escalate takedown and SEO poisoning disablement the moment a threat is confirmed
This transforms brand impersonation protection from an offline forensic task to a real-time security function.
Why Brand Impersonation Has Become Unmanageable
Most enterprises now manage dozens of digital assets across web, mobile, and marketing platforms, each one a potential target for impersonators. To aggravate matters, 75% of phishing links are hosted on good, trusted websites, with up to six days as the average window of exposure before legacy security tools begin blocking pages from zero-hour phishing attacks. Threat actors exploit this complexity to create phishing sites, fake ads, cloned apps, and lookalike domains that divert traffic and harvest credentials.
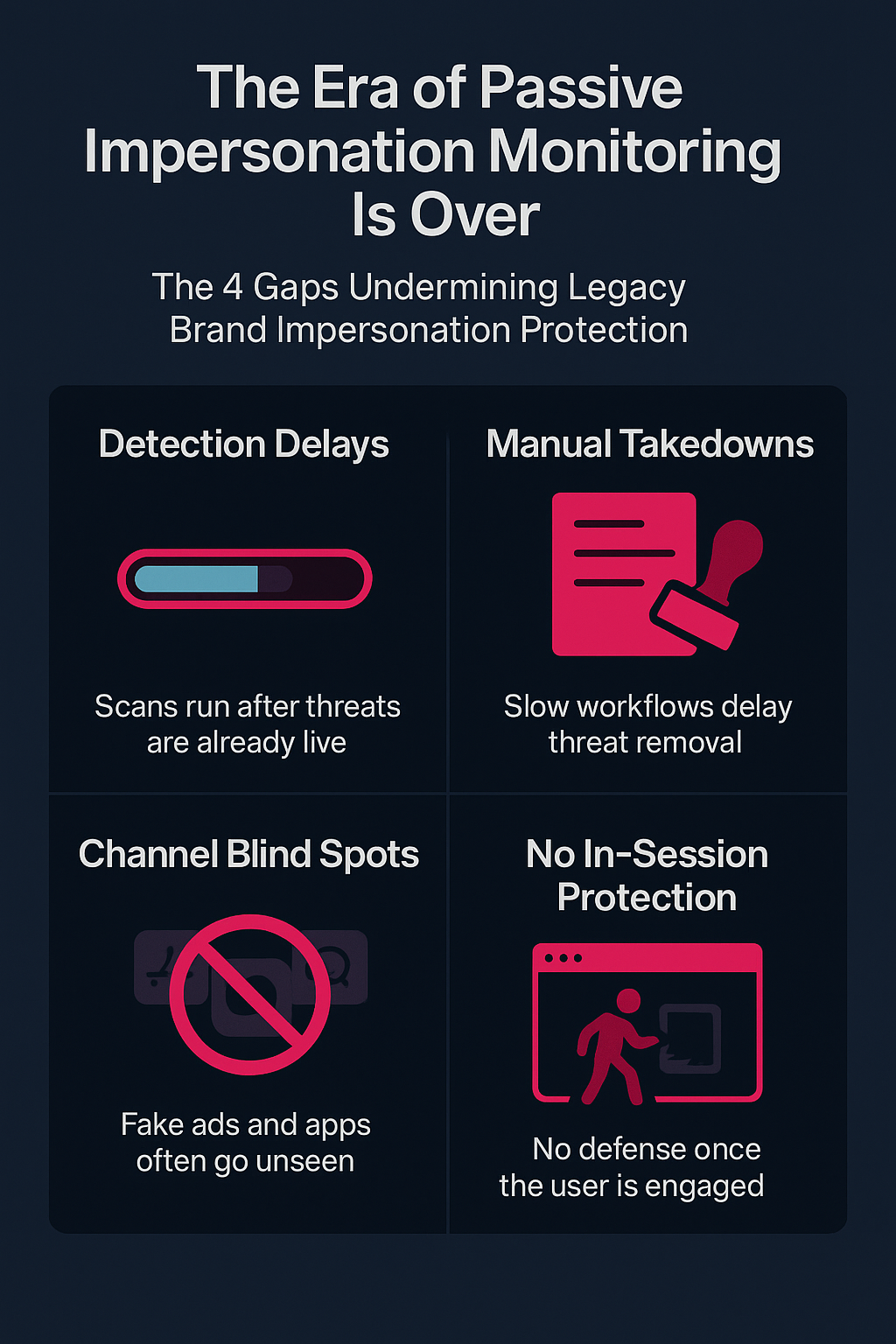
Common gaps in legacy brand impersonation protection strategies include:
- Detection delays: Scans may run hours after a site or ad goes live, well after victims engage.
- Manual takedowns: Disruption depends on slow third-party escalation or legal workflows.
- Channel blind spots: App stores, paid ads, and emerging social platforms are often ignored.
- Lack of real-time user protection: Customers remain vulnerable in-session, even if a threat is detected.
The era of passive impersonation monitoring is over. Scalable brand impersonation protection now demands real-time detection, automated disruption, high-fidelity visibility, and a focus on stopping phishing-driven fraud before it spreads.
Why Legacy Tools Fall Short, and What Memcyco Does Differently
Most traditional impersonation monitoring tools rely on reactive detection models that respond only after users are already exposed, often hours after phishing sites or spoofed ads go live. These approaches are slow to detect, blind to user context, and ineffective at stopping threats before exploitation. Memcyco closes these gaps by combining early reconnaissance detection with real-time browser-level signals triggered on the legitimate site.
| Legacy Approach | Memcyco’s Real-Time Approach |
| Periodic domain scanning | Real-time detection from browser-level signals on the genuine site |
| Manual takedown workflows | Automated takedown initiation and SEO poisoning disablement |
| Post-breach visibility | In-session user protection and real-time visibility into affected users |
| Web-only monitoring | Cross-channel protection: social, mobile, ads, app stores |
Related: What Domain Takedown Services Miss and How to Close the Gap
In short, legacy approaches periodically scan for impersonation threats already actively doing harm, offering zero actionable or investigable insight. In contrast, Memcyco’s technology infiltrates, reveals and disrupts impersonation campaigns in real time from the attack preparation phase, deploying real-time protective measures as attacks evolve.
The result is a closed feedback loop that not only mitigates impersonation threats before they escalate, but also exposes the who, what, where, and how behind each attack – including individual v giving security, fraud, and digital teams the intel they need to respond faster, protect better, and outpace the next wave.
How Memcyco Disrupts Brand Impersonation Threats in Real Time
Memcyco combines early reconnaissance detection with in-session protection and automated takedown , providing full-spectrum defense against impersonation campaigns from start to finish. It detects impersonation campaigns in their early stages, intervenes mid-session to block credential theft, and dismantles attacker infrastructure before trust, data, or revenue are at risk.
Preemptive Threat Recognition
- Website reconnaissance detection: Identifies dev-tool-based inspection activity, often a precursor to site cloning.
- Suspicious domain registration monitoring: Flags spoofed domain attempts designed to mimic brand assets.
- Suspicious device detection: Identifies devices previously linked to phishing sites or high-risk behaviors.
In-Session Scam Disruption
When users interact with the genuine site, Memcyco activates real-time defenses:
- [Optional] Red Alerts: On-page browser warnings when users arrive from known phishing sites.
- Decoy credentials: Injected on phishing sites to mislead attackers and expose credential theft.
- Phishing site visitor detection: Tracks user behavior and origin to identify attack patterns.
- Real-time attack detection: Flags behaviors linked to impersonation-driven fraud attempts.
Infrastructure Neutralization
Memcyco initiates direct countermeasures to disarm attacker infrastructure:
- SEO poisoning defense: Prevents impersonation sites from ranking on search engines.
- Automated takedown initiation: Triggers domain and content takedowns without human delay. Read our guide on How to Choose the Best Domain Takedown Service, and why speed isn’t everything.
- Deception campaigns: Pollutes attacker infrastructure with false data to reduce effectiveness and trace behavior.
These capabilities operate in a continuous detection-response loop, enabling real-time containment, disruption, and visibility into impersonation campaigns at scale.
Considering your options? Read our guide on What to Look for in a Phishing Site Detection and Takedown Solution
Case Study: How Memcyco Helped a Retailer Disrupt an Impersonation Attack Before It Caused Harm
https://www.youtube.com/watch?v=pJOe9f2MBd0
A major European retailer faced persistent impersonation attacks that spawned over 430 impersonating websites.
With over 40 million monthly visitors to its legitimate website, the retailer’s daily login volume made every minute of delayed detection a critical risk to customer credentials, accounts, and other personal data.
More than 100,000 customers were ultimately protected from potential account takeover attempts, thanks to Memcyco’s decoy credentials intercepting logins on fake sites – which were all rapidly neutralized.
The results were immediate:
- Mean time to detection dropped dramatically
- Response became instant and fully automated
- SOC and fraud team workload dropped by 80%
- Impersonation-related customer service escalations declined by 70%, easing pressure on support teams and improving customer trust metrics
“We’re finally able to preempt brand impersonation threats from the attack preparation phase to take proactive measures that prevent costly downstream consequences – while having the piece of mind that customer credentials are theft-proof, even if customers fall for scams” said the company’s security lead.
Your next move: Stop Watching. Start Disrupting.
Memcyco turns impersonation threats from invisible risks into visible, preventable events. If your current tools only alert you after the damage is done, it’s time to upgrade your defense.
Schedule a product tour and discover the secret-sauce technology global enterprises are turning to for getting the upper hand against cross-channel brand impersonation threats.
FAQs About Automated Brand Impersonation Protection
What is automated brand impersonation protection?
Automated brand impersonation protection refers to a system that detects and disrupts impersonation threats across digital environments, in real time and without manual intervention. It includes early detection of spoofed domains and reconnaissance activity, as well as real-time browser-level responses that stop attacks before they escalate into fraud.
How does Memcyco detect brand impersonation threats?
Memcyco detects brand impersonation by monitoring early-stage attacker behaviors such as site reconnaissance using developer tools and suspicious domain registration, and by analyzing browser-level signals when users arrive from spoofed or low-reputation referral sources. These indicators, combined with domain spoofing detection and real-time phishing site identification, provide early and in-session visibility into impersonation campaigns.
Which channels does Memcyco cover?
Memcyco monitors web domains, app stores, paid search and display ads, and social platforms including Facebook, LinkedIn, Telegram, Reddit, TikTok, and more.
How is Memcyco different from a takedown provider?
Most takedown services react only after exposure occurs. Memcyco operates earlier in the chain, detecting impersonation signs during site reconnaissance and intercepting credential harvesting in real time using decoy injections and browser-level alerts.
What makes Memcyco different from traditional monitoring tools?
Most monitoring tools focus on periodic scans and alerting after impersonation assets go live. Memcyco detects impersonation intent during the website reconnaissance stage, also identifying spoofed domains as they’re registered, while activating real-time defenses while users are still at risk. It doesn’t just observe threats, it disrupts them before they escalate.